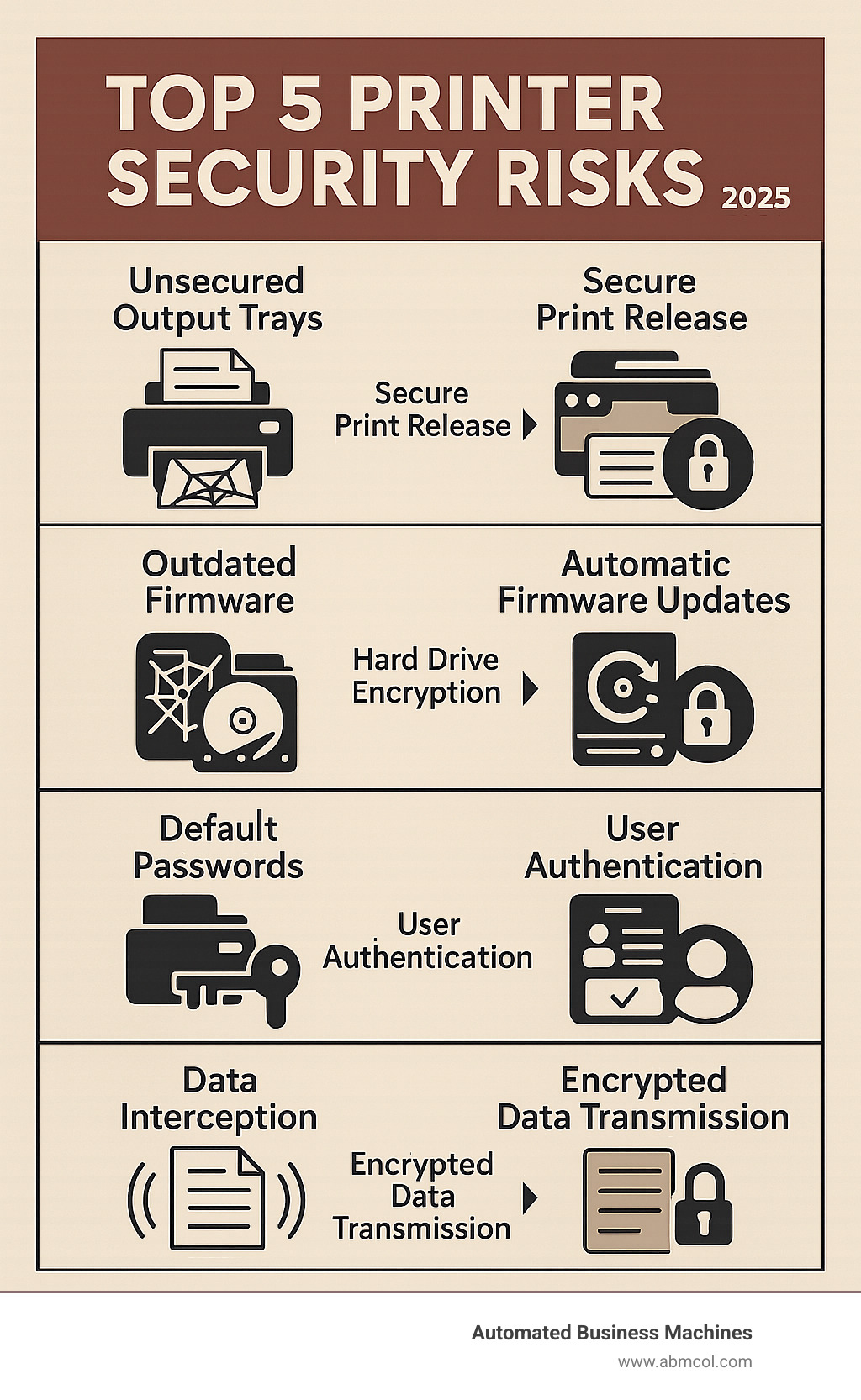
A laser printer secure solution addresses one of the most overlooked vulnerabilities in modern offices. Here’s what you need to know:
Top Secure Laser Printer Features:
- Hard drive encryption (AES 256-bit) for data at rest
- User authentication (PIN, badge, biometrics) for access control
- Secure print release to prevent document theft from output trays
- Firmware protection with automatic security updates
- Network encryption (SSL/TLS, IPSec) for data in transit
The numbers are alarming. Over two-thirds (68%) of organizations have experienced data losses due to unsecure printing in the past year. Your printer is an intelligent network endpoint that stores sensitive data and can be a gateway for cyberattacks.
Employees print sensitive documents like payrolls and contracts daily. Without security, these can be stolen from output trays or from the printer’s internal hard drive—a treasure trove for hackers.
Modern printers are computers that need the same security as laptops and servers. Fortunately, today’s secure laser printers have built-in features to protect your data from start to finish.
Why Your Office Printer is a Major Security Risk
Your office printer is a major security blind spot. A laser printer secure solution isn’t about convenience; it’s about protecting your business from a common attack vector.
Hackers target printers because they are often overlooked as network-connected computers. Unauthorized access can create a backdoor to your entire network.
Data interception is a common threat. Without encryption, documents sent to print travel across your network like postcards, readable by anyone monitoring the traffic.
The risk of stored data theft from hard drives is significant. Many printers store copies of every print job, creating a repository of sensitive documents—from payroll to legal contracts—that is vulnerable to hackers.
Malware and ransomware attacks can spread through unsecured printers just like any other network device, potentially crippling an entire company.
Finally, unsecured output trays pose a simple but costly risk. A confidential document left unattended can be easily stolen, and the breach may go unnoticed until it’s too late.
These vulnerabilities can lead to serious compliance violations with regulations like GDPR and HIPAA, resulting in hefty fines and legal issues.
More info about Data Loss Prevention for Printers
Understanding Common Vulnerabilities
A common mistake is treating printers as “set it and forget it” devices. Like computers, they need regular security maintenance.
Outdated firmware is a dangerous and common vulnerability. Manufacturers release security patches, but if they aren’t installed, printers become easy targets for hackers who actively scan for these known exploits.
Default passwords like “admin” or “password” are a gift to cybercriminals. Failing to change them gives hackers easy access to printer settings.
Open network ports and unencrypted print jobs create additional attack surfaces, allowing anyone with the right tools to intercept and read data as it travels across the network.
Physical tampering is another risk, especially for printers in common areas. Malicious USBs can be installed, settings changed, or hard drives stolen.
More info about Network Vulnerability Assessment vs. Pen Testing
The High Cost of a Breach
A printer security breach has far-reaching consequences. Financial losses are immediate, including costs for forensic investigations, legal fees, and system remediation.
Reputational damage can be even more costly, as a data breach erodes customer trust and can lead to lost business for years.
Regulatory fines under laws like GDPR and HIPAA can be crushing, reaching millions of dollars and threatening business continuity.
Operational downtime during a breach halts business, leading to lost revenue and productivity as employees and customers are impacted.
Perhaps the most devastating consequence is intellectual property theft. Once proprietary designs, strategies, or customer lists are stolen, the damage is permanent.
Investing in printer security costs far less than recovering from a breach. It’s not an expense—it’s insurance for your business’s future.
Key Features of a Top-Tier Laser Printer Secure Fleet
A true laser printer secure solution goes beyond basic printing, offering a fortress of layered security features to protect data at every stage.
When evaluating printers, ask how well they protect data at rest, in use, and in transit. The answers separate true security solutions from basic printers.
Device & Data-at-Rest Security
The heart of any secure printer lies in how it protects data that’s sitting on the device itself. Every time we send a print job, scan a document, or store settings, that information needs bulletproof protection.
Hard drive encryption (AES 256-bit) is the first line of defense. It makes data on a stolen hard drive unreadable.
Secure data erase (compliant with standards like DoD 5220-22.M) is critical for retiring old printers. It overwrites data multiple times, making recovery impossible.
Secure Boot and firmware integrity validation protect the printer’s operating system by checking all software before it runs, preventing tampered code from executing.
Run-time intrusion detection constantly monitors for suspicious activity. Advanced models with self-healing BIOS can automatically detect, stop, and recover from attacks.
More info about Enterprise Secure Printing: Safeguard Your Documents
Access & Data-in-Transit Security
Controlling who can use our printers and protecting data as it travels across our network is just as important as securing the device itself.
User authentication via PIN, badge, or biometrics ensures documents remain locked in the printer until the authorized user releases them.
Role-based access control provides granular control, allowing you to define which users can access specific functions, like scanning or printing sensitive documents.
Encrypted data transmission using protocols like SSL/TLS and IPSec creates a secure tunnel for data, preventing interception on the network.
Network port management improves security by closing unnecessary ports, restricting device access, and disabling USB ports to prevent unauthorized data transfers.
Here’s how security features typically scale for different business needs:
| Security Feature | Small Office Needs | Enterprise Needs |
|---|---|---|
| Device Security | Secure boot with firmware validation | Self-healing BIOS, run-time intrusion detection |
| Data-at-Rest | Write-protected memory, secure cartridges | Hard drive encryption, secure disk erase (DoD) |
| Access Control | Password protection, basic panel lock | Multi-factor authentication, role-based access |
| Data-in-Transit | Basic network security | IPSec, SSL/TLS, datastream encryption |
| Management | Automatic firmware updates | Centralized fleet management, audit trails |
Why a MICR Laser Printer Secure Solution is Essential for Financial Documents
For checks and financial documents, standard security is insufficient. A specialized MICR laser printer secure solution is needed to address the unique risks.
MICR (Magnetic Ink Character Recognition) technology uses special magnetic ink that banks can read electronically. But true security goes far beyond just the right ink.
The Disable Jam Recovery feature is a powerful fraud prevention tool. It prevents the automatic reprinting of a jammed check, eliminating the risk of duplicate checks being created.
Datastream encryption and specialized MICR toner security features protect check data in transit, creating a robust defense against counterfeiting.
Physical security features like paper tray locks prevent theft of blank check stock. Precise positioning technology also helps reduce rejected checks, streamlining financial operations.
For any business handling check printing internally, investing in a secure MICR solution isn’t optional – it’s essential protection for our financial integrity.
Implementing a Rock-Solid Secure Printing Strategy
Secure laser printer secure hardware is just the first step. Like a home security system, it must be properly configured, maintained, and used correctly to be effective.
This section details the practices that transform secure hardware into a comprehensive, real-world security posture.
Adopting a Zero Trust Approach to Printing
Modern cybersecurity uses the Zero Trust principle: “never trust, always verify.” This means no device or user is automatically trusted, even if they are already on the network.
Applying Zero Trust to printing means treating every printer as a potential threat that requires constant verification and monitoring.
Identity Provider (IdP) integration connects printers to your main authentication system. Users must pass full authentication, including MFA, to print sensitive documents.
Micro-segmentation for printers isolates them on the network. If a printer is compromised, the breach is contained and cannot easily spread to critical systems.
Continuous monitoring actively watches for suspicious printer activity, such as unusual access times or network traffic, and sends immediate alerts.
More info about Secure Printing Solutions: 5 Steps to Protect Data
Leveraging Secure Print Release and Management Software
A common, preventable risk is when a confidential document is printed and forgotten in the output tray, where anyone can see it.
Pull printing (or Follow-me printing) solves this. Jobs are held in a secure queue until the user authenticates at any printer, ensuring documents go directly into their hands.
Authentication is convenient via badge, PIN, or mobile app. Some systems even recognize an approaching user and display their print queue automatically.
Centralized fleet management allows you to manage all printers from one dashboard. This simplifies tasks like automated firmware updates, ensuring critical security patches are deployed to every device.
Audit trails for compliance provide a detailed record of every print job: who, what, when, and where. This is invaluable for meeting regulations like GDPR or HIPAA and for investigating security incidents.
More info about Managed Print Services: Benefits & Cost Savings 2025
Training Employees on Secure Printing Practices
Even the best laser printer secure technology can be undermined by human error. Employee training is crucial to prevent mistakes like leaving sensitive documents in output trays.
The key is to help employees understand that secure printing protects everyone’s data, including their own personal information.
Recognizing sensitive documents is foundational. Train staff that items like customer lists, schedules, and internal memos can be as sensitive as contracts or financial reports.
Using secure release features becomes second nature when employees understand why it’s important. Explain how pull printing protects their privacy and prevents data exposure.
Reporting suspicious activity fosters a culture of shared responsibility. Encourage employees to report unattended documents or unusual printer activity.
Proper document disposal is crucial. Teach staff to use secure shredding bins for all confidential documents, not the regular recycling.
Finally, ensure everyone knows how to use private print modes and PIN releases for their most confidential documents.
Effective training involves hands-on practice with the actual printers. Confident employees are more likely to use security features consistently.
Frequently Asked Questions about Secure Laser Printers
Here are answers to common questions about improving printing security.
How do I secure mobile and cloud printing?
Securing mobile and cloud printing is essential. With the right approach, you can have both convenience and security.
Secure mobile printing apps are your first line of defense. They encrypt print jobs and require authentication for release, keeping documents in a secure queue until you are at the printer.
Enforcing authentication for cloud job release is critical. Use services that require robust verification, like MFA, to prevent unauthorized printing.
Always use encrypted connections (SSL/TLS) for data traveling between devices, the cloud, and your printer. Wi-Fi Direct is another option that allows direct connection without using the main network.
Vet your cloud service providers thoroughly. Check their encryption, access controls, certifications, and data handling policies. Ensure they provide audit trails for all print activity.
More info about Secure Document Print
Can I make my existing printers more secure?
You don’t need to replace your entire printer fleet to improve security. While a new laser printer secure solution has the latest features, you can effectively improve your current setup.
Managed print services (MPS) are a powerful solution for existing fleets. An MPS provider can centralize security, manage firmware updates, and implement secure print release across all your devices.
Print management software can add pull printing capabilities to older models, holding jobs until user authentication. This eliminates the risk of unattended documents.
Don’t overlook the basics. Regularly updating firmware and changing default passwords are simple but critical steps to prevent breaches.
A professional security assessment identifies specific vulnerabilities, helping you invest your security budget for the biggest impact.
More info about Cyber Security Assessment Services
How does a secure laser printer help with GDPR compliance?
A secure printer simplifies GDPR compliance, acting as a safety net for data protection requirements.
Controlling access to personal data is fundamental to GDPR. User authentication ensures personal data only reaches authorized hands, preventing exposure from output trays.
Audit trails are a GDPR lifesaver, creating detailed logs of print activity (who, what, when, where) for accountability and regulatory requests.
Data encryption protects personal information at rest and in transit. Hard drive encryption ensures stored data is unreadable if a device is stolen, meeting GDPR’s security requirements.
Secure deletion capabilities help meet GDPR’s “right to be forgotten.” Features like DoD-compliant secure erase permanently remove personal data from printer storage.
Secure printers help enforce your data handling policies. They integrate with your IT framework to restrict printing and ensure consistent processes for handling personal data.
Conclusion
As we’ve explored laser printer secure solutions, it’s clear that office printers are sophisticated network endpoints requiring the same security attention as laptops and servers.
We’ve covered the key security pillars: device-level protection (encryption, secure boot), access controls (user authentication), and processes (Zero Trust, employee training).
The right hardware is only the first step. Features like AES 256-bit encryption are foundational, but a bulletproof security posture requires a holistic strategy combining secure devices, access controls, and defined processes.
Think of it like securing a house: a strong front door isn’t enough. You need secure walls and windows, a security system, and people who know how to use them. Your printing environment is no different.
A holistic strategy is essential for true protection. Look beyond individual features to your entire print workflow. Consider how employees handle sensitive documents, the security of mobile printing, and whether you have compliance-ready audit trails.
At Automated Business Machines, we understand every business has unique security challenges. We specialize in customized, advanced technology solutions that grow with your business. As a locally owned and operated company serving businesses throughout Georgia, we’ve seen how the right secure printing strategy transforms an organization’s confidence in its data handling.
Don’t let your printers be the weak link in your security chain. With the right combination of secure hardware, smart processes, and ongoing support, your printing environment can become a competitive advantage, not a vulnerability.