AI Overview:
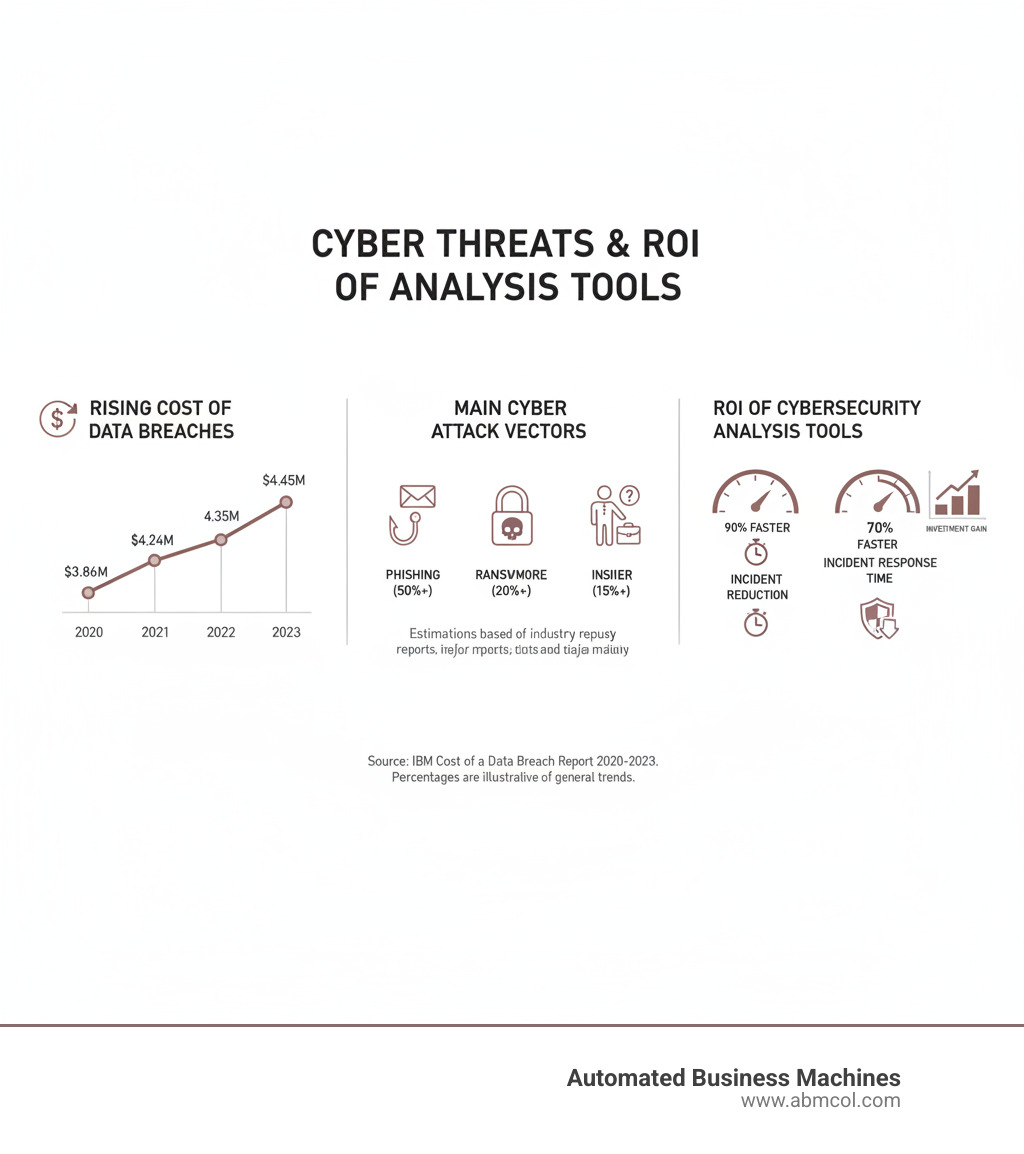
Cybersecurity analysis tools have become indispensable for modern organizations as digital threats grow more sophisticated and costly. With the average data breach reaching $4.45 million in 2023 and 95% of incidents tied to human error, these tools act as the first and strongest layer of defense.
Why Cyber Security Analysis Tools Are Your First Line of Defense
Cyber security analysis tools are essential software that helps organizations detect, analyze, and respond to digital threats. With the average cost of a data breach hitting $4.45 million in 2023 and 95% of breaches caused by human error, these tools are critical for business survival.
Here are the main types of cyber security analysis tools every organization needs:
- Network Security Monitoring Tools – Monitor traffic and detect suspicious activity (Wireshark, Nagios)
- Vulnerability Scanners – Identify security weaknesses before hackers do (Nmap, OpenVAS, Nessus)
- SIEM Platforms – Collect and analyze security data from multiple sources (Splunk, ELK Stack)
- Endpoint Protection – Secure individual devices and workstations (antivirus, EDR solutions)
- Penetration Testing Tools – Simulate attacks to test defenses (Metasploit, Burp Suite)
- Data Loss Prevention (DLP) – Protect sensitive information from unauthorized access
The cybersecurity market is projected to reach $534.27 billion by 2032, reflecting that cyber threats are evolving faster than ever. Traditional reactive approaches are no longer enough.
Modern cyber security analysis tools don’t just respond to attacks—they predict and prevent them. They use AI and machine learning to spot patterns, automate security tasks, and provide the real-time visibility that security teams need.
For businesses managing connected devices, cloud services, and remote workers, these tools are as essential as locks on the front door. The question isn’t whether you need them—it’s which ones will best protect your specific environment without breaking your budget.
What Are Cyber Security Analysis Tools and Why Are They Crucial?
Think of cyber security analysis tools as digital security guards, working 24/7 to monitor thousands of data points, spot patterns, and respond to threats in real-time. With data breaches costing millions and most caused by human error, these tools have become absolutely crucial for catching what we might miss.
These tools serve four primary purposes:
Threat detection is like a 24/7 digital security camera, continuously scanning your network for suspicious activity, unusual data transfers, or malicious software.
Incident response provides a lightning-fast, automated emergency plan when an attack occurs, giving clear information on the impact and required actions.
Compliance helps you meet regulatory requirements like HIPAA or GDPR by automating reports and maintaining the necessary security standards.
Risk reduction is about proactive prevention, helping you find and fix vulnerabilities before hackers can exploit them.
This shift to a proactive defense keeps you ahead of threats. For businesses looking to build this foundation properly, our Cyber Security Frame Work Guide provides a roadmap for creating comprehensive protection.
The Core Benefits of Using Security Analysis Tools
Investing in cyber security analysis tools builds a stronger, more confident business. The core benefits include:
Improved threat visibility provides a clear view of your digital environment, showing attempted attacks and weak points before they become major problems.
Faster incident response drastically cuts down investigation time from days to minutes, which can be the difference between a minor issue and a catastrophe.
Automated detection and remediation uses AI to spot and sometimes automatically fix threats, working 24/7 to isolate infected devices or block suspicious traffic.
Regulatory compliance is simplified by automatically generating audit logs, enforcing data policies, and creating the reports needed for regulators.
Reduced financial risk is the ultimate benefit. By preventing costly breaches, these tools offer a significant return on investment, a fact reflected in the rapidly growing security analytics market.
For organizations that want these benefits without the complexity, Managed Security Solutions provide expert oversight and 24/7 monitoring.
How Different Tools Fortify Your Defenses
Cyber security analysis tools work together to create multiple layers of protection, a concept known as “defense in depth.”
Network monitoring tools act as watchtowers, analyzing network traffic to learn what’s normal and flagging any unusual activity immediately.
Vulnerability scanning proactively scans your systems, applications, and devices for known security weaknesses, much like a daily security inspection. Our Cyber Security Assessment Services can help you understand where your vulnerabilities lie.
Endpoint protection secures every endpoint (laptops, smartphones, etc.), stopping threats at the device level before they can spread to the network.
Data encryption scrambles your data into an unreadable format, protecting it both in storage and during transit. Even if stolen, the information is useless to attackers.
Log analysis sifts through millions of log entries from your systems, connecting the dots to identify attack patterns and provide forensic details for investigations.
The Arsenal: Primary Categories of Cyber Security Tools
A strong cybersecurity defense requires a combination of specialized tools working together. Each category of cyber security analysis tools serves a specific purpose in your digital defense toolkit.
These tools complement each other: network tools monitor traffic, vulnerability scanners find weak spots, SIEMs act as command centers, and DLP tools protect data. Let’s explore how they fit into a security strategy.
Network Security & Monitoring Tools
Your network is a prime target for attackers, making network security and monitoring tools your digital watchtowers.
Packet sniffers like the popular Wireshark capture and examine individual data packets, revealing details like unencrypted passwords or suspicious communication.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) like Snort act as an early warning system. An IDS alerts you to threats, while an IPS actively blocks them.
Real-time traffic analysis is invaluable for instantly analyzing traffic to spot anomalies. These tools use anomaly detection by establishing a baseline of normal activity to flag anything out of the ordinary.
Regular assessment is crucial. Our Network Security Assessment Key Benefits and Steps guide can help. For wireless networks, see our Wireless Network Security Assessment Guide.
Vulnerability Scanners & Penetration Testing Tools
Vulnerability scanners and penetration testing tools help you think like an attacker to find and fix weaknesses before they are exploited.
Vulnerability scanners like Nmap, OpenVAS, and the industry-standard Nessus identify security flaws, misconfigurations, and outdated software, providing detailed reports on your exposures.
Penetration testing tools simulate cyberattacks to test defenses, often using a Red Team versus Blue Team approach. Red teams attack, while blue teams defend.
Red team tools like Metasploit (for exploits) and Burp Suite (for web app testing) are used to find vulnerabilities. Blue team tools use insights from these tests to improve defenses. Some tools, like Nessus Essentials, help both identify vulnerabilities and verify fixes.
This proactive approach is essential. Our Network Assessment Services can help you implement these tools and interpret their findings.
SIEM & Log Management Tools
SIEM (Security Information and Event Management) and log management tools bring order to the chaos of security data from across your network.
Data aggregation is the foundation. SIEMs collect logs and event data from all sources—firewalls, servers, endpoints—into one place.
Log correlation uses advanced algorithms to connect seemingly unrelated events, turning raw data into actionable intelligence.
Centralized monitoring provides a single dashboard for real-time visibility, replacing the need to check dozens of individual logs. Popular platforms include Splunk and the open-source ELK Stack.
Threat intelligence feeds integrate real-time data on known malicious IPs and attack patterns, allowing the SIEM to flag activities linked to global threats.
Forensic analysis is crucial after an incident. The detailed historical logs help investigators trace an attacker’s steps and understand the scope of a compromise.
Data Loss Prevention (DLP) & Document Security Tools
Data loss prevention (DLP) and document security tools are essential for protecting your most valuable asset: your data.
DLP solutions monitor, detect, and block sensitive data from leaving your organization. They protect data in use (on devices), in motion (across networks), and at rest (in storage).
Encryption is the backbone of data protection. It scrambles information into unreadable code, ensuring it remains safe even if stolen.
Access controls ensure only authorized users can access specific data or systems through authentication and role-based permissions.
At Automated Business Machines, we understand data security extends to physical documents. Our approach includes Secure Printing Services Protect Your Data and specialized Data Loss Prevention for Printers. We also offer broader Document Security Solutions for Business and a robust Document Management System to protect your information throughout its lifecycle.
How to Select the Right Cyber Security Analysis Tools
Choosing the right cyber security analysis tools can be overwhelming. Since there’s no one-size-fits-all solution, a methodical approach based on your specific needs is key.
Start with a needs assessment. What are you protecting? Customer data, financial records, or intellectual property? Understanding your risk profile helps you choose the right tools.
Consider the total cost of ownership, including licensing, implementation, maintenance, and training. The cheapest option isn’t always the most cost-effective.
Scalability is crucial. Your security needs will grow with your business, so choose solutions that can scale with you.
Integration capabilities are vital. Tools must integrate with your existing tech stack (email, cloud services) to avoid creating inefficient data silos.
Finally, consider the open-source versus commercial trade-offs. Open-source tools offer flexibility but require technical expertise, while commercial tools provide support and ease of use at a higher cost.
Key Features to Look For in Cyber Security Analysis Tools
When evaluating tools, look for these game-changing features:
- Real-time analysis: Essential for continuous monitoring and immediate alerts. Early detection can prevent a minor incident from becoming a major disaster.
- Automation: Automatically responds to common threats, reducing alert fatigue and freeing up your team to focus on complex issues.
- Integration: Tools must integrate smoothly with your existing tech stack, like Microsoft 365 or Google Workspace. For custom needs, our Custom Technology Solutions for Business Success can help.
- Usability: An intuitive interface is critical. A powerful tool is useless if your team can’t use it effectively.
- Reporting: Translates technical data into business-relevant insights, helping demonstrate value and meet compliance requirements.
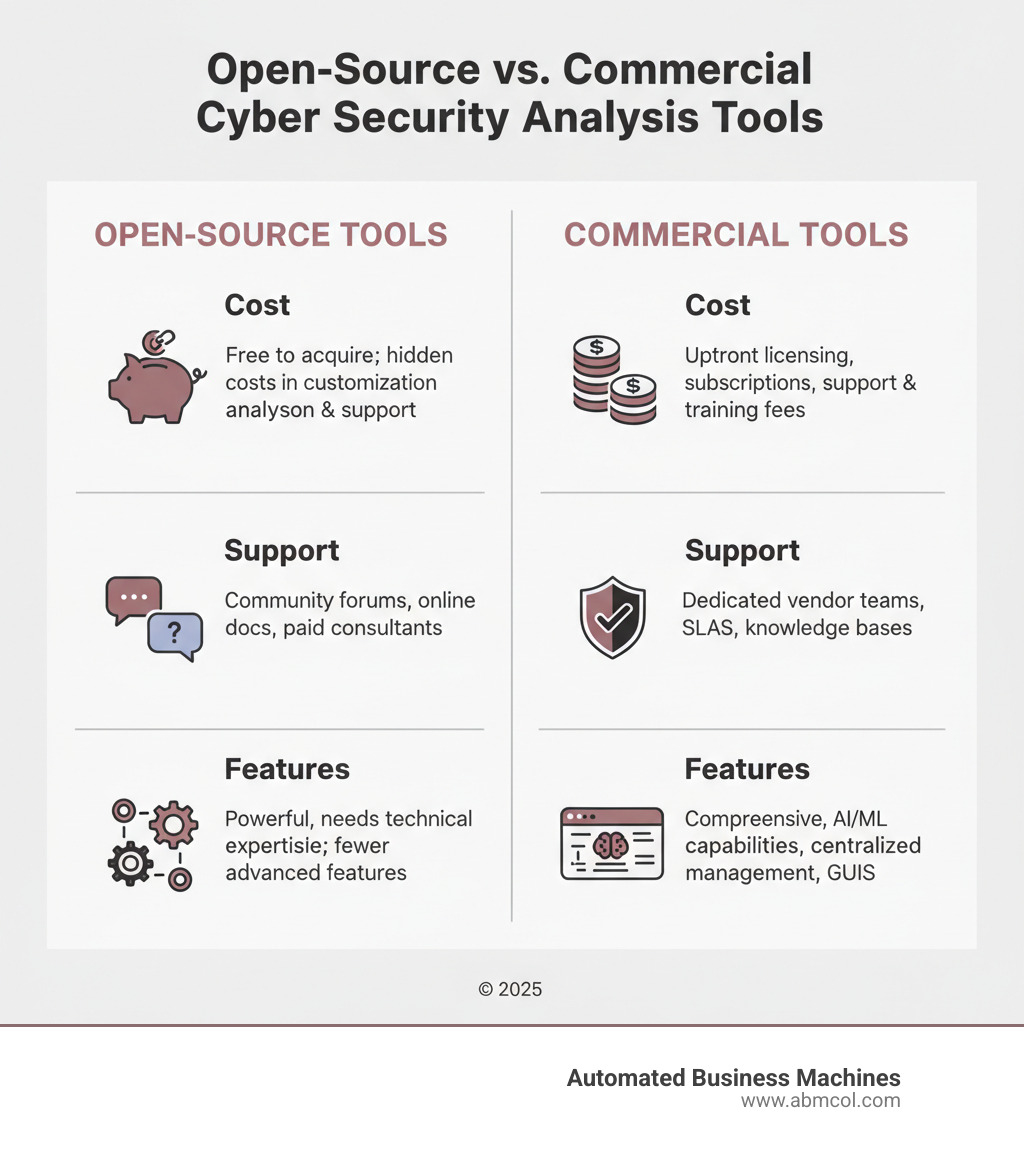
Open-Source vs. Commercial Tools: A Strategic Choice
Choosing between open-source and commercial tools depends on your organization’s budget, technical capabilities, and needs.
| Feature | Open-Source Tools | Commercial Tools |
|---|---|---|
| Cost | Typically free to acquire, but may have hidden costs for customization, integration, and support. | Upfront licensing fees, subscriptions, and potentially additional costs for support and training. |
| Support | Community-driven forums, online documentation, and potentially paid third-party consultants. | Dedicated vendor support teams, SLAs, knowledge bases, and professional services. |
| Features | Can be powerful but often require significant technical expertise to configure and integrate. May lack some advanced features. | Comprehensive feature sets, often with advanced capabilities like AI/ML, centralized management, and intuitive GUIs. |
| Customization | Highly customizable; source code is available, allowing for tailoring to specific needs (requires developer skills). | Limited customization options, typically through configuration settings or APIs provided by the vendor. |
| Ease of Use | Often requires a higher level of technical proficiency for setup and ongoing management. | Generally more user-friendly with graphical interfaces and streamlined workflows. |
| Updates | Community-driven; updates can be frequent but may lack a formal release schedule or rigorous testing. | Regular, scheduled updates and patches from the vendor, often with extensive testing and quality assurance. |
| Compliance | May require significant effort to demonstrate compliance, as certifications are less common for individual tools. | Vendors often provide certifications (e.g., ISO, SOC 2) and features designed to aid in compliance reporting. |
Open-source tools like Wireshark or OpenVAS are powerful and flexible if you have in-house technical expertise. However, consider the hidden costs of setup, customization, and maintenance.
Commercial solutions offer a smoother implementation with dedicated support and user-friendly interfaces. They are often better for organizations that need to get running quickly or lack deep technical resources.
A hybrid approach is often best, using open-source tools for specific tasks and commercial solutions for critical functions. This maximizes value while ensuring professional support where it’s needed most. Be honest about your resources and goals—the objective is effective security, regardless of the tool type.
The Future of Cyber Defense: Emerging Trends and Skills
The world of cybersecurity is constantly evolving. Staying ahead means embracing the cutting-edge technologies and skills that will define tomorrow’s digital battleground.
The Rise of AI and Machine Learning in Security
AI and machine learning are revolutionizing threat detection, analysis, and response. The use of AI in this field is growing by 20% annually.
What makes AI so powerful is its ability to spot patterns that humans would miss:
- Behavioral analytics is a key application. AI learns your environment’s normal behavior and flags any deviations, such as an employee accessing sensitive data at an unusual time or location.
- Automated threat hunting allows AI to autonomously scan massive datasets for threats, connecting dots that human analysts might miss.
- Alert fatigue is reduced as AI prioritizes alerts and filters out false positives, allowing analysts to focus on real threats.
- Predictive analysis uses historical data and threat intelligence to anticipate future attacks, enabling proactive defense.
Essential Skills for Mastering Security Tools
Even with smarter tools, skilled professionals are critical for interpreting results and making strategic decisions. The most important skills include:
- Programming skills, especially in Python, are highly valuable for automating tasks and analyzing data. Knowledge of JavaScript, PHP, and SQL is also useful depending on the role.
- Analytical thinking is essential for interpreting data, identifying patterns, and drawing conclusions to understand the context behind security events.
- Continuous learning is mandatory in this rapidly changing field. Professionals stay current through self-study, training, and certifications like CISSP, CompTIA Security+, CISM, and CEH.
- Problem-solving is fundamental. The ability to troubleshoot, innovate, and adapt under pressure is what defines a great security professional.
The future belongs to those who can blend technical expertise with strategic thinking, combining the power of advanced cyber security analysis tools with uniquely human insights.
Frequently Asked Questions about Cyber Security Analysis Tools
Cybersecurity can feel overwhelming. Here are answers to the most common questions we hear about cyber security analysis tools.
What is the most fundamental cybersecurity tool for a small business?
There's no single "magic bullet" tool. Small businesses need a layered approach that covers the basics affordably. Just as you'd use locks, cameras, and an alarm for a physical office, digital security requires multiple layers.
Fundamental components include firewalls (your first line of defense) and antivirus/endpoint protection to secure individual devices. However, the single most impactful measure is Multi-Factor Authentication (MFA), which stops most password-based attacks.
Don't forget regular backups—they are your ultimate safety net when all else fails.
For small businesses wanting comprehensive security without the internal management headache, our Managed IT Services Benefits 101 guide explains how professional support can provide enterprise-level protection.
Do I need to know how to code to use cybersecurity analysis tools?
The short answer is no, not for most entry-level roles, but coding skills will accelerate your career. Many modern tools have user-friendly graphical interfaces that require no programming.
However, coding (especially Python) is a major asset for automating tasks, customizing tools, and performing advanced analysis. For advanced roles like penetration testing, coding is nearly essential. Many professionals are self-taught, so it's an accessible skill to learn.
How do these tools help with compliance like HIPAA or GDPR?
These tools turn compliance nightmares into manageable, automated processes, helping you avoid the steep fines associated with regulations like GDPR and HIPAA.
Audit Logs: They provide detailed, automated logs to track who accessed what data and when, which is crucial for audits.
Access Control: They enforce policies to ensure only authorized users can access sensitive data.
Data Encryption: They automatically encrypt data in storage and in transit to meet compliance requirements.
Reporting: They generate comprehensive, customizable reports to demonstrate compliance with regulatory standards.
At Automated Business Machines, we understand compliance extends to physical documents. Our Secure Document Print solutions ensure your paper-based processes also meet strict regulatory standards.
Conclusion
In today’s digital landscape, cyber security analysis tools are essential for survival. With evolving threats and data breaches costing millions, they are as critical as locks on your office doors.
A layered defense approach is key. Combining network monitoring, vulnerability scanning, SIEM, and endpoint protection creates a robust security ecosystem that is difficult for attackers to penetrate.
The modern approach is proactive, not reactive. AI-powered tools help predict and prevent threats, which is a transformative shift from simply responding to attacks after they occur.
Success requires continuous assessment of your unique risks and security posture. The tools you choose must adapt as your business and the threat landscape evolve.
Considering the immense cost of a data breach—both financial and reputational—investing in these tools is a critical investment in your company’s future.
For a comprehensive approach, secure office technology must integrate with robust IT strategies. At Automated Business Machines, we understand security extends beyond networks to include every document and workflow. Our IT Services are designed to create a unified security ecosystem that protects your entire business operation, from your network infrastructure to your physical document handling processes.
The future belongs to businesses that take cybersecurity seriously today. With the right tools, the right approach, and the right partners, you can build defenses that don’t just protect your business—they give you the confidence to innovate and grow without fear.