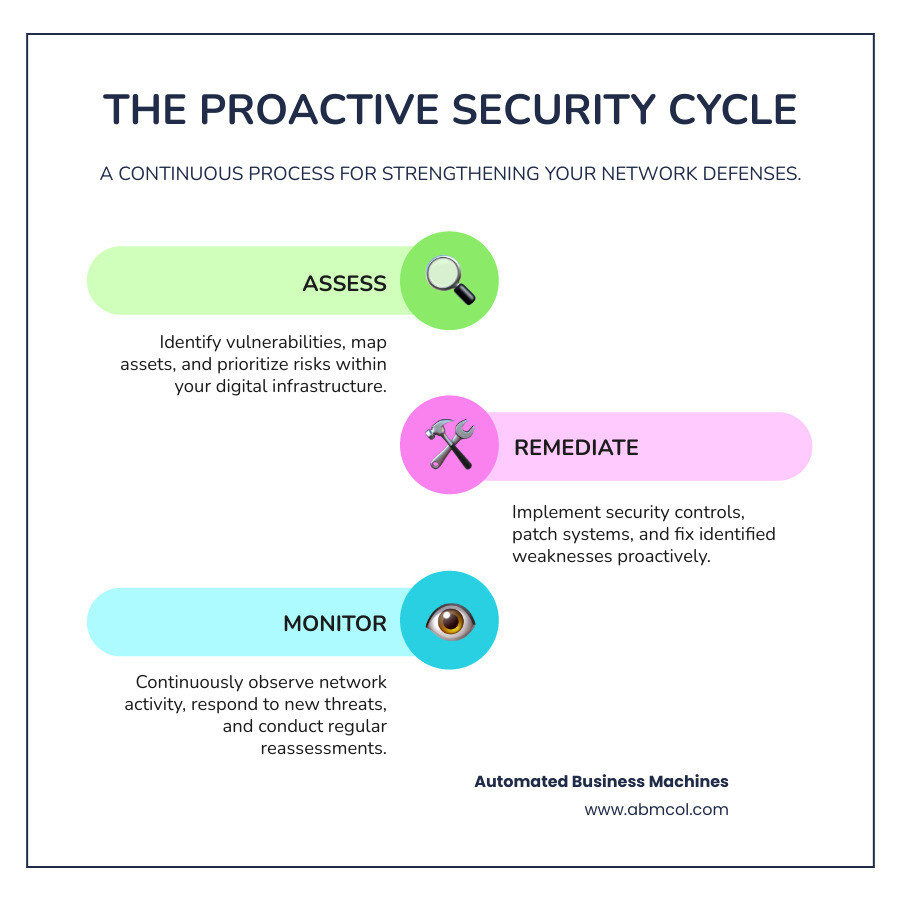
A network and security assessment is a deep dive into your digital infrastructure, like a health check-up for your network. It helps you find weak spots, identify risks, and strengthen your security.
It’s crucial for several reasons:
- Prevent breaches: Stop cyberattacks before they happen.
- Protect data: Safeguard sensitive information, from client records to financial details.
- Meet compliance: Adhere to industry rules like HIPAA or PCI DSS.
- Save money: Proactive assessments cost far less than recovering from a major data breach.
The assessment process typically involves:
- Mapping your network and all connected devices.
- Finding vulnerabilities and misconfigurations.
- Testing defenses by simulating attacks.
- Prioritizing risks to fix the most critical issues first.
- Implementing new security measures and solutions.
- Continuously monitoring your network for new threats.
In today’s digital world, your business network is always under attack. The global average cost of a data breach reached $4.88 million in 2024, a 10% increase from the previous year, with 422.61 million records compromised in Q3 alone. These figures show that cyber threats are growing and expensive.
This is why a network and security assessment is essential. It moves you from a reactive stance—fixing problems after they hit—to a proactive one. You find the cracks before attackers do. This systematic review is about understanding your vulnerabilities and strengthening your defenses.
This guide will cover the steps involved, the benefits for your business, and the tools that make it possible.
Why a Network Security Assessment is Non-Negotiable
For any business, network security is a matter of survival. A comprehensive network and security assessment is a proactive step to find hidden weaknesses and transform them into strengths, keeping your operations smooth and your reputation intact.
These assessments are about business survival. They pinpoint weak spots and vulnerabilities before a cyberattack can strike, drastically reducing the risk of damage. This proactive approach protects your data, prevents downtime, and safeguards your reputation, saving you from costly recovery efforts.
At Automated Business Machines, we offer in-depth network and security assessments to build a solid partnership with you. By securing your network, we help you build trust with your clients. As your trusted security advisors, we ensure you’re always ahead of the curve, leading to stronger security and lasting client relationships.
Beyond business continuity, these assessments are vital for compliance management. Industries like healthcare (HIPAA), finance (PCI DSS), and retail (GDPR) have strict rules. Assessments identify where regulated data is at risk, allowing us to recommend smart protections. By helping you meet these standards, we help you avoid hefty fines and legal troubles.
Finally, assessments offer crucial financial protection and help avoid costly downtime. They empower you to manage risks, plan resources, and protect critical data. The ongoing improvements we uncover mean your security stays strong against new threats, resulting in fewer unexpected costs and less disruption.
To dive deeper into how we help businesses stay secure, check out our Managed Security Solutions and our helpful Cyber Security Frame Work Guide.
Types of Assessments: Choosing the Right Approach
Just as different ailments require specific medical tests, various security needs call for specific types of network and security assessments. Understanding these is key to choosing the right approach for your organization.
Here are the primary types we use:
- Vulnerability Assessment: This is a comprehensive scan that identifies potential weaknesses in your network, like checking for open uped doors. It uses automated tools to find known vulnerabilities, misconfigurations, and outdated software. The goal is to provide a prioritized list of security flaws that could be exploited.
- Penetration Testing (Pen Test): While a vulnerability assessment points out potential issues, a pen test actively simulates a real-world cyberattack. An “ethical hacker” attempts to exploit identified weaknesses to see how far an attacker could get and what data they could access. Pen tests can use various methods:
- Black Box Testing: Simulates an external attacker with no prior knowledge of the system.
- Gray Box Testing: Simulates an attacker with limited knowledge, like an insider threat.
- White Box Testing: Simulates an attacker with full knowledge of the system to test specific logic.
- Compliance Assessment: This assessment audits your security controls against specific industry standards like HIPAA, PCI DSS, or GDPR. The goal is to verify that your security practices meet regulatory requirements and help you avoid penalties.
- Configuration Review: This is a detailed examination of the security settings of your network devices, servers, and applications. Misconfigurations are a common source of vulnerabilities, and this review ensures controls are properly implemented according to security policies.
- Wireless Security Assessment: This assessment focuses on your wireless networks, including Wi-Fi and IoT devices. It identifies vulnerabilities in access points, encryption, and device configurations to prevent unauthorized access. You can learn more in our Wireless Network Security Assessment Guide.
Understanding the nuances between these assessments is crucial. For a more detailed comparison, check out our article on Network Vulnerability Assessment vs. Pen Testing.
Here’s a quick comparison:
| Assessment Type | Scope | Goal | Frequency |
|---|---|---|---|
| Vulnerability Assessment | Broad scan of systems, applications, network devices | Identify and list potential security weaknesses. | Quarterly, bi-annually, or after significant changes. |
| Penetration Testing | Targeted, in-depth test of specific systems | Actively exploit weaknesses to demonstrate real-world impact and bypass security controls. | Annually, or after major changes to critical systems. |
| Compliance Assessment | Specific controls and policies relevant to regulations | Verify adherence to regulatory standards (e.g., HIPAA, PCI DSS, GDPR). | As required by regulation (e.g., annually, bi-annually). |
How to Conduct a Comprehensive Network and Security Assessment: A 5-Step Guide
Conducting a thorough network and security assessment is a clear roadmap to a more secure future. We follow a systematic, five-step approach to uncover every potential weak spot and help you build strong defenses.
Step 1: Define Scope and Map Your Assets
The first step is defining the assessment’s scope and creating an asset inventory—a detailed record of all hardware (servers, computers, printers) and software. We document details for each item, including its network address, OS, and business criticality. Overlooked devices like printers can be a security risk, which is where our secure printing solutions expertise is valuable. For more tips, see our Printer Security Best Practices Guide for Offices.
Next is data classification, which helps us understand the value and sensitivity of your information. We consider the potential impact of a breach—financial penalties, reputational damage, and recreation costs—to prioritize what needs the most protection.
We also use network mapping tools to visualize all connected devices and data flows. This map often reveals “hidden” devices or unapproved software, known as shadow IT, which are significant security blind spots.
Step 2: Identify Threats and Scan for Vulnerabilities
With a network map, we identify potential threats and scan for vulnerabilities. This involves understanding common cybercriminal tactics and looking for weaknesses they could exploit.
Common threats include:
- Malware and Ransomware: Often delivered via phishing emails.
- Phishing and Social Engineering: Tricking people into revealing credentials.
- Misconfigurations: Simple setup errors that expose sensitive information.
- Outdated Software and Unpatched Systems: A major entry point for attackers.
- Weak Passwords and Open Ports: Easy targets for unauthorized access.
- Unauthorized IoT Access: Smart devices with default, unchanged passwords.
We use threat intelligence, like the MITRE ATT&CK framework, to understand attacker behaviors. Then, we perform vulnerability scanning, using automated tools to check your entire digital setup for known weaknesses. This is a crucial step to find cracks before attackers do.
For a deeper look at how we identify these security gaps, explore our Cyber Security Assessment Services.
Step 3: Assess Impact and Prioritize Risks
Finding vulnerabilities is just the start; the next step is to understand their business impact and prioritize them. Not all risks are equal.
We use a risk matrix to weigh the potential consequences of each vulnerability, considering data loss, downtime, financial costs, and reputational damage. By assessing the likelihood of a threat and its potential impact, we assign a risk level: Critical, High, Medium, or Low. This focuses our efforts on what matters most. For example, a flaw in a public-facing website is more urgent than one in an internal test system.
We also consider cascading effects—how one system failure could affect other business areas. The average time to fix a network vulnerability is over 60 days, highlighting why quick action on high-risk vulnerabilities is critical. Our goal is always to secure your most important business assets first.
Step 4: Implement Mitigation and Security Controls
With risks prioritized, it’s time to implement solutions. We create a custom remediation plan with clear, actionable steps to strengthen your defenses.
Key security controls include:
- Patch Management: Keeping all software and systems up-to-date to fix known vulnerabilities.
- Access Controls: Applying the principle of least privilege so users only have necessary access. We also help set up multi-factor authentication (MFA).
- Network Segmentation: Dividing your network into isolated sections to contain breaches.
- Firewalls and IDS/IPS: Deploying firewalls and Intrusion Detection/Prevention Systems to monitor and block malicious traffic.
- Encryption: Protecting sensitive data both at rest and in transit.
- Layered Security: Using multiple security measures so that if one fails, others provide backup.
- Secure Configurations: Disabling unused network ports and using modern, secure protocols.
- Employee Training: Updating security policies and training your team to spot phishing and practice secure habits is vital, as human error is a major factor in breaches.
For businesses handling sensitive documents, our Document Security Solutions for Business can further boost security by preventing data leaks in your printing environment.
Step 5: Create a Response Plan and Monitor Continuously
Even with strong defenses, incidents can occur. The final, ongoing step is to have a plan and remain vigilant.
An incident response plan is critical. It outlines exactly what to do if a breach occurs, including forming a rapid response team, establishing communication channels, and detailing recovery steps. A ready plan minimizes damage and downtime.
Continuous monitoring is also a must. We use tools that constantly watch for threats and changes, providing real-time alerts. This helps us spot misconfigurations, outdated software, and other emerging weaknesses.
Regular reassessments are just as important. We recommend a full network and security assessment at least annually, or more often for regulated industries or after major network changes. This ongoing process ensures your security keeps pace with your business and the evolving threat landscape.
By constantly checking, testing, and evaluating your cybersecurity, we help clients stay one step ahead. To learn more about our continuous security offerings, check out our Managed Security Services.
Conclusion: Turning Your Assessment into a Stronger Security Posture
A network and security assessment is a strategic investment in your business’s foundation. It’s a proactive step that protects your data, ensures compliance, and builds a more resilient future for your company.
Here are the key takeaways:
First, be proactive rather than reactive. Catching issues before they become crises saves money, stress, and reputational damage.
Second, security is a continuous process. The digital landscape is always changing, so ongoing vigilance, regular reassessments, and continuous monitoring are essential to stay ahead.
For us, delivering these assessments is about building trust. The actionable insights from an assessment provide peace of mind and guide smart security improvements, strengthening our partnership and positioning us as your dedicated security advisors.
At Automated Business Machines, we are a locally owned and operated business serving communities like Albany, Athens, Atlanta, Auburn, Augusta, Columbus, Johns Creek, LaGrange, Macon, Marietta, Newnan, Roswell, Sandy Springs, and Savannah, GA. Our expertise extends beyond traditional IT to include secure printing solutions and digital workflows. We provide customized technology solutions that boost productivity and bake security into your core operations.
By embracing regular network and security assessments, you’re not just protecting data; you’re safeguarding your reputation and ensuring business continuity.
Ready to take the next step? Learn more about our comprehensive IT services and how we can strengthen your security posture by visiting us at abmcol.com/it-services/.
How often should we conduct a network security assessment?
We recommend a full assessment at least annually to stay ahead of changing cyber threats.
However, businesses in highly regulated industries like healthcare or finance may need more frequent assessments—bi-annually, quarterly, or even monthly—to meet strict compliance requirements.
It's also crucial to conduct an assessment after any significant IT changes, such as major system upgrades, network expansions, or mergers and acquisitions, as these events can introduce new vulnerabilities.
Can a small business perform its own assessment?
While a small business can perform basic assessments in-house using available tools, a truly comprehensive network and security assessment requires deep expertise and specialized tools. Without a professional eye, subtle but critical vulnerabilities can be missed.
Partnering with a professional vendor provides:
Deeper insight: Uncovering hidden risks automated tools miss.
Objective perspective: An external view to spot blind spots.
Advanced tools: Simulating real-world attacks effectively.
Actionable recommendations: Clear guidance on how to fix problems.
When choosing a partner, look for proven experience, a clear methodology, and transparent reporting. Ask about their team's certifications, such as CISSP (Certified Information Systems Security Professional), CEH (Certified Ethical Hacker), or CISA (Certified Information Systems Auditor), which demonstrate a high level of expertise.
What's the difference between a vulnerability assessment and a penetration test?
This is a great question. Think of your network as a house.
A vulnerability assessment is like checking for open uped doors and windows. It uses automated scans to identify potential weaknesses and create a list of security flaws. It tells you where you might be vulnerable.
A penetration test is like trying to pick the locks and sneak through an open window. It actively exploits those weaknesses to see if an attacker could get in and what they could access. It tells you how an attacker could get in and what they could do.
In short, a vulnerability assessment identifies potential issues, while a penetration test confirms if they are exploitable. For a detailed comparison, read our article on Network Vulnerability Assessment vs. Pen Testing.