Network security assessment is crucial for understanding and improving an organization’s cybersecurity posture. As cyberattacks become more sophisticated, this process helps pinpoint vulnerabilities in your IT infrastructure before they can be exploited. Let’s break down why this assessment is essential:
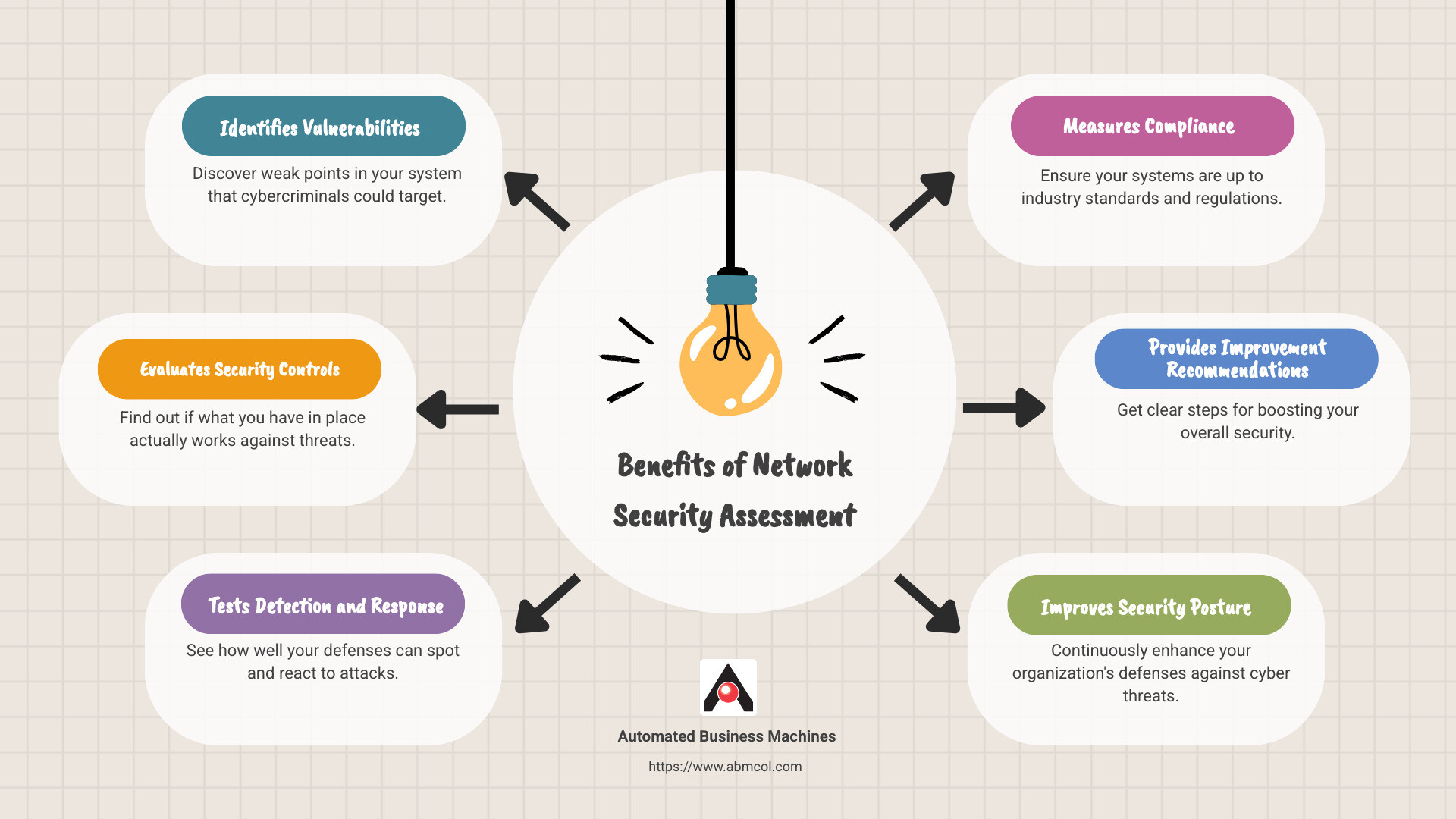
- Identifies vulnerabilities: Find weak points in your system that cybercriminals could target.
- Evaluates security controls: Find out if what you have in place actually works against threats.
- Tests detection and response capabilities: See how well your defenses can spot and react to attacks.
- Measures compliance: Ensure your systems are up to industry standards and regulations.
- Provides improvement recommendations: Get clear steps for boosting your overall security.
It’s an ongoing effort to keep your organization’s data safe and secure.
Understanding Network Security Assessment
A network security assessment is like a health check-up for your IT systems. It examines your network to find weaknesses that could be exploited by cybercriminals. The goal? To make sure your data stays safe and your systems work smoothly.
Definition
At its core, a network security assessment is an audit of your IT infrastructure. It looks for potential security holes and evaluates how well your current defenses hold up. Think of it as a detective, searching for clues to keep your network safe from harm.
Purpose
The primary purpose of a network security assessment is to identify vulnerabilities before they become serious threats. By checking your network’s defenses, you can be proactive rather than reactive. This means you’re not just waiting for an attack to happen—you’re ready for it.
Importance
Why is this so important? Well, cyberattacks are becoming more sophisticated every day. A network security assessment helps you stay a step ahead by identifying weak spots and suggesting ways to fix them.
This process also checks if your security controls are effective. Are your firewalls and encryption methods up to par? An assessment will tell you.
Compliance Requirements
Many industries have strict regulations to protect sensitive data. For example, healthcare organizations need to comply with HIPAA, while businesses handling credit card information must meet PCI DSS standards. A network security assessment ensures you’re following these rules, avoiding hefty fines and keeping trust with your clients.
In short, a network security assessment is a vital part of maintaining a strong cybersecurity posture. It helps you spot potential problems, fix them, and keep your network safe from the changing landscape of cyber threats.
Types of Network Security Assessments
When it comes to keeping your network safe, there are three main types of assessments you should know about: vulnerability assessment, penetration testing, and risk assessment. Each plays a unique role in safeguarding your IT environment.
Vulnerability Assessment
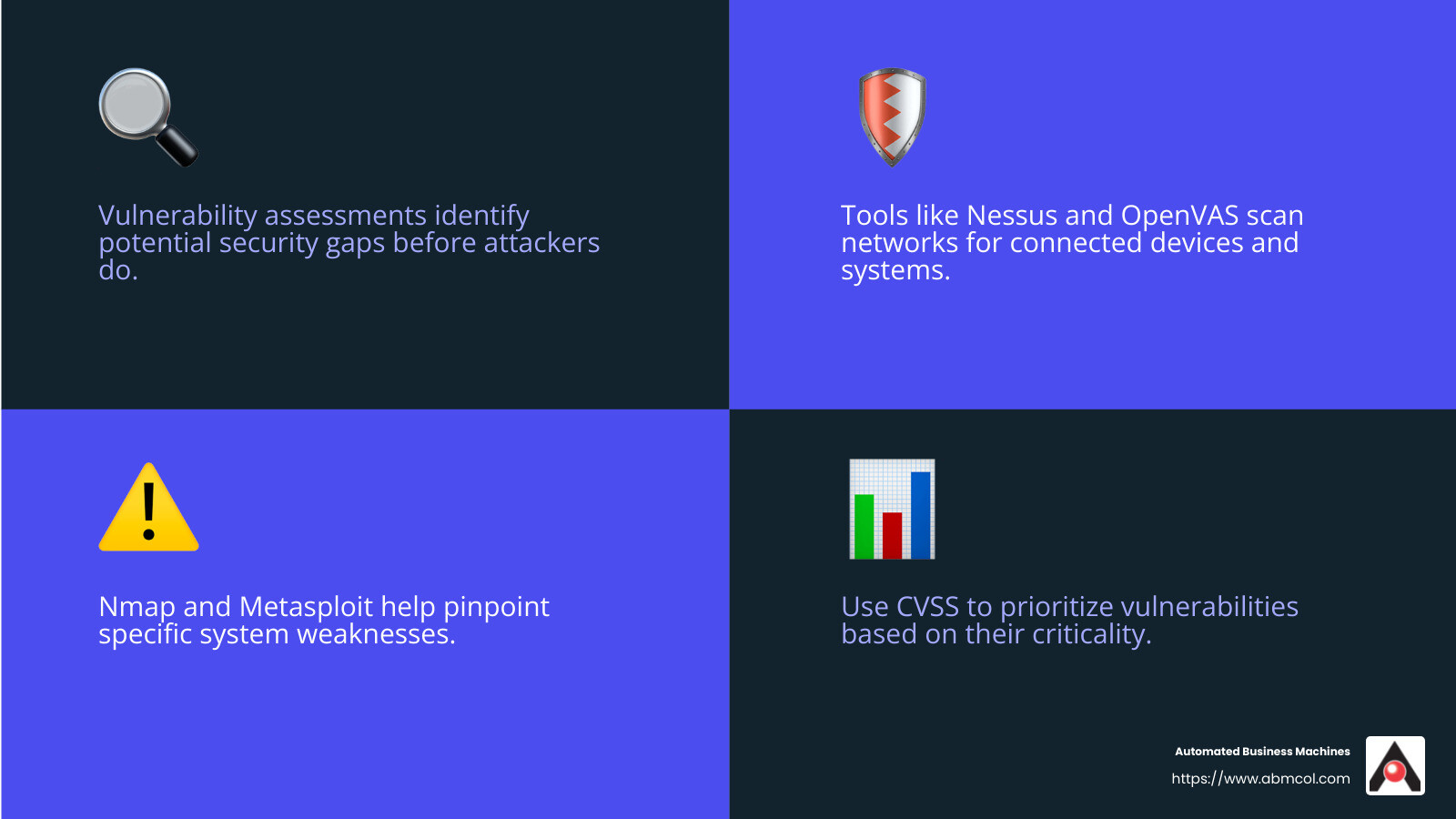
Think of a vulnerability assessment as a detailed inspection of your network. Its main goal is to find weaknesses before hackers do. It involves scanning your systems, applications, and devices to spot vulnerabilities that could be exploited.
Here’s how it works:
- Scanning the Network: Tools like Nessus and OpenVAS scan your network to find connected devices and systems.
- Identifying Vulnerabilities: Tools such as Nmap and Metasploit help pinpoint specific weaknesses in your systems.
- Prioritizing: Not all vulnerabilities are equal. Some are more critical than others. The Common Vulnerability Scoring System (CVSS) helps prioritize which ones to fix first.
- Reporting: A detailed report is created, outlining the vulnerabilities found, their severity, and recommendations for fixing them.
Penetration Testing
Penetration testing, or pen testing, is like a fire drill for your network. It simulates a real-world attack to see how your defenses hold up. Conducted by ethical hackers, pen testing goes beyond just identifying vulnerabilities—it tests how they could be exploited.
The process typically involves:
- Planning and Reconnaissance: Defining the scope and gathering information about the target systems.
- Exploitation: Attempting to breach your network defenses to assess their robustness.
- Analysis: Reviewing the results to identify successful attack vectors and potential improvements.
Risk Assessment
A risk assessment evaluates the potential impact of identified vulnerabilities on your organization. It considers the likelihood of a threat exploiting a vulnerability and the potential damage that could result.
Key steps include:
- Identifying Assets: Knowing what you’re protecting is crucial. This includes data, hardware, and software.
- Analyzing Threats: Understanding what types of threats could impact your network.
- Evaluating Impact: Assessing how a breach could affect your operations, finances, and reputation.
- Mitigation Planning: Developing strategies to reduce or eliminate risks.
In summary, these assessments work together to provide a comprehensive view of your network’s security. They help you identify vulnerabilities, understand potential impacts, and strengthen your defenses. This proactive approach is essential in today’s changing threat landscape.
Conducting a Network Security Assessment
Starting on a network security assessment is like building a fortress around your digital assets. It involves several key steps that ensure your network remains secure and resilient against threats.
Inventory Resources
Start by taking stock of what you have. This means identifying all your network assets—servers, applications, devices, and data. You can’t protect what you don’t know exists. Prioritize these assets based on their importance to your business. This step is crucial because it helps you focus your security efforts where they matter most.
Assess Vulnerabilities
Once you know what you’re working with, it’s time to find the cracks. Use automated tools to scan your network for vulnerabilities. These tools can spot weak spots in your system that hackers might exploit. Not all vulnerabilities are created equal. Some pose a greater risk than others, so prioritize them accordingly.
Test Defenses
Now, it’s time to see how your defenses hold up. Simulate cyber attacks to test your security measures. This step often involves penetration testing, where ethical hackers try to breach your defenses. The goal is to identify any weaknesses in your security posture before malicious actors do.
Document Results
After testing, document everything. Create a detailed report that outlines the vulnerabilities you found, their potential impact, and recommendations for remediation. This report serves as a roadmap for improving your network security. It helps you understand where you stand and what needs to be done to improve your defenses.
Implement Controls
With your report in hand, it’s time to act. Implement security controls to address the vulnerabilities identified. These controls can be technical, like firewalls and encryption, or physical, like locks and biometrics. They can also be preventative, like multi-factor authentication, or detective, like intrusion detection systems.
Continuous Monitoring
Security is not a one-time task. Continuously monitor your network for new vulnerabilities and threats. This involves regular security assessments and real-time monitoring tools that alert you to suspicious activity. By staying vigilant, you can respond quickly to new threats and keep your network secure.
By following these steps, you can build a robust security framework that protects your network from evolving threats. Up next, we’ll explore the benefits of conducting regular network security assessments.
Benefits of Regular Network Security Assessments
Regular network security assessments are like routine check-ups for your digital health. They provide a comprehensive review of your network’s security posture, ensuring your defenses are always up to par. Here are the key benefits:
Identify Vulnerabilities
The primary goal of these assessments is to uncover hidden vulnerabilities. By regularly scanning and testing your network, you can find weak spots before cybercriminals do. This proactive approach means you can fix issues early, reducing the risk of a security breach.
Measure Impact
Understanding the potential impact of each vulnerability is crucial. Not all security gaps are equal; some can lead to minor inconveniences, while others might cause significant damage. Regular assessments help you prioritize vulnerabilities based on their potential impact, allowing you to allocate resources effectively.
Improve Security Measures
With each assessment, you gain valuable insights into your network’s security. These insights guide you in refining and enhancing your security measures. Whether it’s updating your firewall, improving encryption, or implementing new policies, continuous improvements keep your defenses strong against evolving threats.
Meet Compliance
For many businesses, meeting industry regulations and compliance standards is non-negotiable. Regular network security assessments ensure you stay compliant with standards like HIPAA, PCI DSS, and others. By demonstrating compliance, you not only avoid costly penalties but also build trust with your clients and partners.
Incorporating these regular assessments into your security strategy ensures that your network remains resilient and robust. Next, we’ll dive into common questions about network security assessments, shedding light on their importance and execution.
Frequently Asked Questions about Network Security Assessment
What is a network security assessment?
A network security assessment is like a health checkup for your organization’s IT infrastructure. It evaluates your network’s security posture by identifying vulnerabilities that could be exploited by hackers. This process aims to uncover weak spots in your defenses, ensuring your network is secure against unauthorized access and data breaches.
Security assessments not only help in identifying current vulnerabilities but also provide insights into how these weaknesses could impact your business operations. By understanding your security posture, you can take proactive steps to strengthen your defenses.
What are the two types of network security assessments?
There are two main types of network security assessments: vulnerability assessments and penetration testing.
- Vulnerability Assessment: This involves scanning your network to identify potential vulnerabilities. Tools like Nessus and OpenVAS help in detecting weaknesses in systems, applications, and network infrastructure. The goal is to find and prioritize vulnerabilities based on their severity and potential impact.
- Penetration Testing: Often referred to as “pen testing,” this method simulates real-world attacks to test your defenses. Ethical hackers try to exploit vulnerabilities to see how far they can go within your network. This hands-on approach provides a deeper understanding of how your security measures hold up against actual threats.
Both methods are crucial for maintaining a strong security posture. While vulnerability assessments help in identifying potential risks, penetration testing provides insights into how those risks could be exploited in real-world scenarios.
How often should network security assessments be conducted?
The frequency of conducting network security assessments depends on several factors, including industry regulations, the size of your organization, and your risk tolerance.
- Industry Regulations: Some industries, like healthcare and finance, have strict compliance requirements that mandate regular security assessments. For example, healthcare organizations in the U.S. need to comply with HIPAA regulations, which often require frequent assessments.
- Risk Tolerance: Organizations with a low tolerance for risk may choose to conduct assessments more frequently to ensure they stay ahead of potential threats.
As a general rule of thumb, it’s recommended to perform network security assessments at least annually. However, if there are significant changes to your IT infrastructure, such as new systems or major upgrades, additional assessments may be necessary. Regular assessments help in maintaining a robust security posture and ensuring compliance with industry standards.
Conclusion
At Automated Business Machines, we understand the importance of keeping your network secure. Our network security assessment services are designed to protect your business from cyber threats and ensure compliance with industry standards. By identifying vulnerabilities and implementing advanced security measures, we help safeguard your IT infrastructure.
Our approach to security is not one-size-fits-all. We offer customized technology solutions that cater to the unique needs of your organization. Whether it’s secure printing, digital workflows, or comprehensive network assessments, we tailor our services to improve your productivity and workflow. With locations across Georgia, including Atlanta, Savannah, and Augusta, we’re committed to providing local support and expertise.
By partnering with us, you gain access to cutting-edge security technologies and a team of experts dedicated to keeping your network safe. Our goal is to give you peace of mind, knowing your business is protected from potential threats.
For more information on how we can help secure your network, visit our IT Services page. Let’s work together to improve your security posture and keep your business running smoothly.